Blocking Robocalls - SHAKEN & STIR
January, 2019
By Aaron Fosdick, CISSP (LinkedIn)
How many robocalls have you been receiving lately, and what are the Government and Telecom Industry doing about them?
In my case, the number has dropped in the first weeks of 2019, but for much of the last year, I could expect 3-5 per day, and always one during dinnertime. The calls are typically spoofed using my area code and prefix "neighbor spoofing". Good thing I kept my number from when I lived in the bay area, since it makes it much easier to identify these calls.
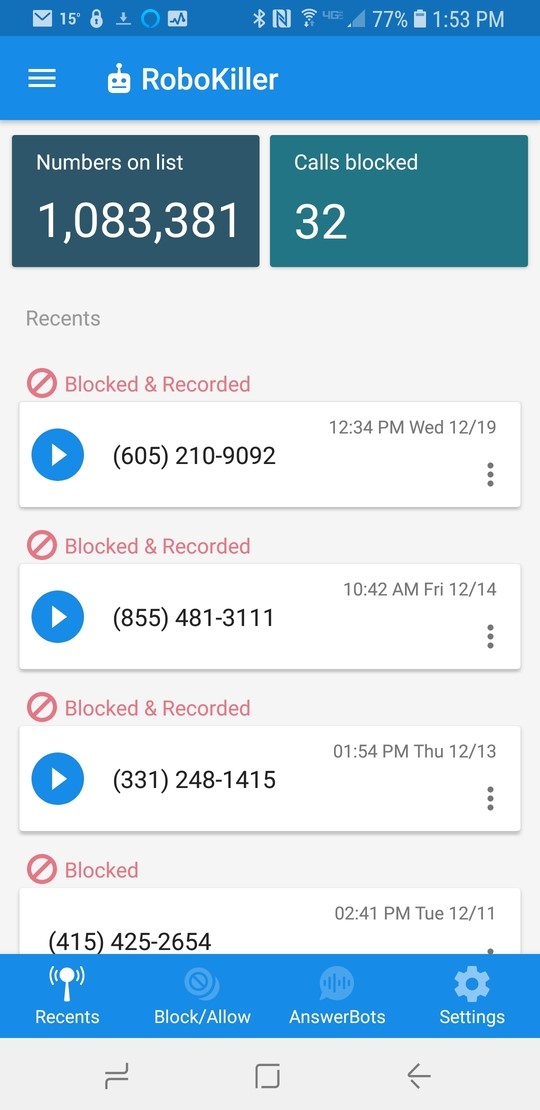
I eventually got fed up and purchased a mobile app called Robokiller. This app is nice not just because it intercepts robocalls, but it has the option to engage the caller with various answer bots. "hello… hello? hello??". It records the conversation and provides both hilarity, and some satisfaction that the telemarketer's time is tied up. The service has a database of over one million known bad numbers, plus technology to identify area-code+prefix calls.
 |
 |
While the Robokiller recordings are fun to share at parties, and the app is well worth the price, it’s not perfect since some calls still do get through when a robocaller uses a random number or something not in their database. I still rarely answer calls from numbers I don’t recognize.
Anyone who has spent time researching telephony knows that the problem originates with SIP, a mature VoIP technology for voice calls. It’s trivial to spoof caller-ID numbers because there is no source of authority attesting that the caller ID number is genuine. Robocallers route their calls through multiple CLECs, obscuring the true call origin. For instance, in Asterisk, you can set any arbitrary number with “${CALLERID(number)”:
/etc/asterisk/extensions_custom.conf
; Customization: Add a trunk predial hook to examine the outbound caller ID number and set the
; outbound caller ID name based on the number (a workaround for a foreign PBX that cannot set the caller ID name string)
[macro-dialout-trunk-predial-hook]
; add log output to show outgoing caller ID information before any changes are made
; note: don't comment out the first line without modifying the new actual first line of code to be sequence number 1
exten => s,1,NoOp(CUSTOM: calleridall is ${CALLERID(all)})
exten => s,n,NoOp(CUSTOM: calleridnumber is ${CALLERID(number)})
; test number case for debugging: override outgoing caller name and caller ID number for calls set to have the outgoing caller ID number to <span id="gc-number-0" class="gc-cs-link" title="Call with Google Voice">555-555-1212</span> (remove comments to enable)
;;exten => s,n,ExecIf($["${CALLERID(number)}" = "+15555551212"]?NoOp(CUSTOM: Setting Caller ID override for source ${CALLERID(number)}))
; exit back
exten => s,n,MacroExit()
Until recently, there has been little incentive for the phone carriers to standardize security standards. But with the increase in robocall volume, the telecom industry has been under pressure to adopt common ‘industry standard’ anti-spoofing technologies. The relevant standards are:
- STIR (Secure Telephone Identity Revisited)
- SHAKEN (Signature-based Handling of Asserted Information Using toKENs)
- PASSporT (Personal Assertion Token – RFC8225 )
STIR is the name chosen by the IETF working group that is finalizing the technical framework for caller authentication using X.509 credentials, meaning there is an authority (CA) that attests that caller-ID numbers are valid. It covers a set of telephony protocols including PASSporT, and the SHAKEN extension.
SHAKEN provides end-to-end encrypted authentication and verification of the telephone caller’s identity (caller ID). It provides the ability for call originators to crypographically sign calls, therefore asserting ownership. It is not designed to encrypt the call data, just the identity.
PASSporT “defines a method for creating and validating a token that cryptographically verifies an originating identity or, more generally, a URI or telephone number representing the originator of personal communications”
SHAKEN Reference Architecture
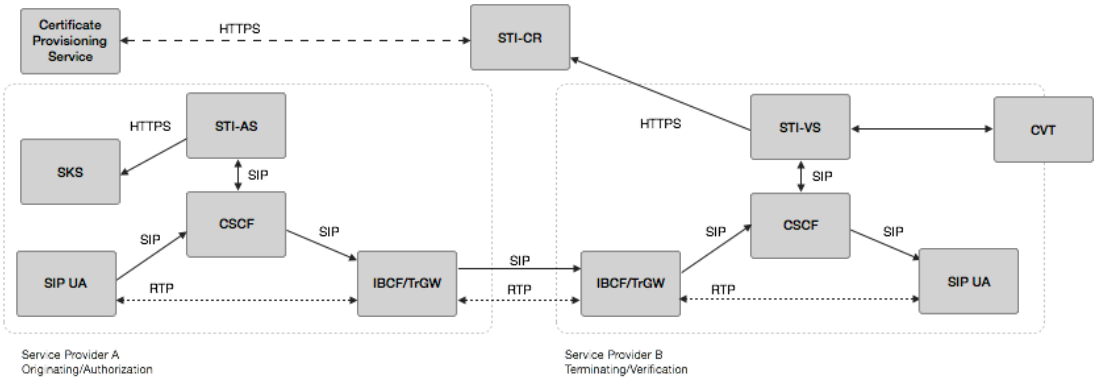
Congress has taken notice of the spoofing problem. In March 2018, the house passed the “Ray Baumes Act”, expanding the definition of Spoofing to include calls and text messages originating outside the US and laying the legal framework for future enforcement actions.
In 2017, the FCC also began taking serious interest in the SHAKEN/STIR framework with a court filing and request for public comments. At that time, they stated that spoofing is their “top consumer priority”. Then, this last November, they sent letters to mobile carriers asking for (demanding) adoption timelines. As expected with government “demands”, many of the responses were less than stellar (read them here), essentially pushing back on the benefit of standardization by stating that SHAKEN/STIR is insufficient and won’t make a difference. The FCC has also been somewhat active in fining US based telemarketing operations who were caught spoofing numbers.
Of course the challenge with any new standard is that until there is industry-wide adoption, the mobile carriers will likely just allow non-authenticated calls to pass through to end users (perhaps marked as soft-fail like with email SPF records). Several mobile carriers have already complained of high implementation costs, which doesn’t bode well for a speedy implementation. They have also stated that while SHAKEN/STIR provides positive attestation that a caller-ID is legitimate, it doesn’t provide the opposite, that a call is fraudulent. While I agree that there is a cat & mouse game with robocallers, this seems disingenuous to me. Just look at this response from Sprint:
“Sprint has not implemented blocking of invalid, unallocated, or unassigned numbers despite the Commission’s order permitting it to do so. Sprint’s data does not show that robocalls from these numbers constitute a significant part of the problem.”
Conversely, T-Mobile has taken a much more proactive approach by deploying internal anti-robocall technology, and is now implementing SHAKEN/STIR. They already identify and notify customers of potential spam calls.
Going forward, most mobile carriers will implement reputation based logic to weed out the majority of robocalls. A call that has been signed using the SHAKEN/STIR protocols will have a much higher reputation than an unsigned call, just like a spam score. The cat and mouse game will continue, with telemarketers coming up with new methods of circumventing the new controls.
As a consumer, your mobile carrier may one day allow you to control whether you accept non-authenticated calls. Until widespread adoption occurs, if robocalls are a real issue for you, install an app such as Robokiller. Also look through the carrier responses to the FCC and choose a forward-thinking carrier.
Postscript:
in January, Verizon announced that they will be implementing SHAKEN/STIR to alert customers to spoofed calls. They join T-Mobile which has been doing it for a while now.